Apr
26
TTT Part 2 of n – Commands
Filed Under System Administration, Computers & Tech on April 26, 2013 | 3 Comments
This is the second instalment of an on-going series. In the first instalment I tried to give you a sort of 40,000ft view of command shells – some context, some history, a very general description of what command shells do, and a little bit on why they are still very useful in the modern GUI age. The most important points to remember from last time are that command shells execute commands, that there are lots of different command shells on lots of different OSes, but that we will be focusing on Bash on Linux/Unix in general, and Bash on OS X in particular. The vast majority of topics I plan to discuss in these segments will be applicable on any system that runs Bash, but, the screen shots I use will be from OS X, and some of the cooler stuff will be OS X only. This segment, like all the others will be used as part of my bi-weekly Chit Chat Across The Pond (CCATP) segment with Allison Sheridan on the NosillaCast Mac Podcast.
Last time I focused on the shell, and avoided getting in any way specific about the actual commands that we will be executing within the Bash shell. I thought it was very important to make as clear a distinction between command shells and commands as possible, so I split the two concepts into two separate segments. Having focused on command shells last time, this instalment will focus on the anatomy of a command, but will start with a quick intro to the Terminal app in OS X first.
Apr
13
TTT Part 1 of n – Command Shells
Filed Under Computers & Tech, System Administration on April 13, 2013 | 6 Comments
I have no idea whether or not this idea is going to work out, but on this week’s Chit Chat Across the Pond segment on the NosillaCast Mac Podcast (to be released Sunday evening PST) I’m going to try start what will hopefully be an on-going series of short un-intimidating segments to gently introduce Mac users to the power contained within the OS X Terminal app. I’m on with Allison every second week, and I’ll have other topics to talk about, so the most frequent the instalments in this series could be would be bi-weekly, but I think they’ll turn out to be closer to monthly on average. While the focus will be on OS X, the majority of the content will be equally applicable to any other Unix or Linux operating system.
In the last CCATP we did a very detailed segment on email security, and despite the fact that with the benefit of hind-sight I realise it was too much to do at once and should have been split into two segments, it received the strongest listener response of anything of any of my many contributions to the NosillaCast in the last 5 or more years. I hope I’m right in interpreting that as evidence that there are a lot of NosillaCast listeners who want to get a little more technical, and get their hands dirty with some good old-fashioned nerdery!
Dec
29
OS X Service for Stripping Geotags from JPEG Images
Filed Under Photography, My Projects, Software Development, Computers & Tech on December 29, 2012 | 1 Comment
Back in 2011 I wrote a blog post explaining how to create an OS X Service for stripping keywords from image files. In this post we’ll use the same technique to create a Service for stripping geotags from JPEG images.
As with the keyword stripping service, there are two prerequisites for this action, one is required, one is optional. You absolutely MUST have install EXIFTool installed, and it would be good if you also had Growl installed, but it’s not essential.
Aug
4
Making an XKpasswd Automator Action
Filed Under My Projects, Software Development, Computers & Tech on August 4, 2012 | 2 Comments
 A few weeks ago on the Chit Chat Across the Pond segment of the Nosillacast, I mentioned that I had an OS X service set up to generate a random password using my XKpasswd Perl module and copy it to the clipboard. Listeners enquired as to how they would go about doing that, so as promised, here’s a quick tutorial.
A few weeks ago on the Chit Chat Across the Pond segment of the Nosillacast, I mentioned that I had an OS X service set up to generate a random password using my XKpasswd Perl module and copy it to the clipboard. Listeners enquired as to how they would go about doing that, so as promised, here’s a quick tutorial.
Obviously this tutorial is for Mac OS X users only, because OS-wide Services and Automator are OS X features. The screenshots are taken on 10.8 Mountain Lion, but this same technique definitely also works on OSX 10.7 Lion, and probably even on 10.6 Snow Leopard. This tutorial also assumes that you have downloaded the XKpasswd module, and saved it somewhere on your computer, along with either the sample dictionary file included with the module or one of your own making, and that you know where on your computer those files have been saved. In other words, you need to have XKpasswd.pm and a text file with one word per line somewhere on your hard drive. In my sample code I’m going to assume you’ve installed the Perl module to the suggested location, /usr/local/xkpasswd/XKpasswd.pm, and that you have customised the sample dictionary a little (more secure that way), and saved it to /usr/local/xkpasswd/dict.txt.
Jun
2
Why the Death of “Save As” is a Good Thing
Filed Under Computers & Tech on June 2, 2012 | 5 Comments
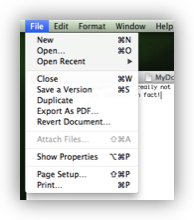 Recently, I was part of a very lively discussion on Twitter between myself and a few Mac users on the replacement of
Recently, I was part of a very lively discussion on Twitter between myself and a few Mac users on the replacement of Save As with Duplicate in OS X 10.7 Lion. Everyone in the conversation but me was angry about it, while I think it’s a fantastic step forward, and just a very small piece of a much bigger picture. The discussion on Twitter included three podcasters, myself, Allison Sheridan of the Nosillacast Mac Podcast, and Mike Potter from For Mac Eyes Only. I suggested the topic could be great fun for a podcast discussion, and the others agreed, so this weekend’s Chit Chat Across the Pond segment on the Nosillacast will be a three way discussion between myself, Allison & Mike on this topic. While preparing my notes though, I realised that I should go beyond just writing a few bullet points, and instead construct a fully formed argument in the form of a blog post, so here it is 🙂
Apr
7
A Quick Tester for Trojan-Downloader:OSX/Flashback
Filed Under My Projects, Security, Computers & Tech on April 7, 2012 | 42 Comments
Update – 13 April 2012: Apple have released another update to Java (via software update) which automatically disables Java in Safari, and removes Flashback if it has infected your system. Please use Apple’s update rather than relying on this script!
Update – 10 April 2012: I have edited the script to run the additional commands recommended by TidBITS. The Download button will now return version 0.2 of the script.
It’s finally happened, there has been a serious malware outbreak on the Mac. Over half a million Macs have been infected with the latest variants of the Flashback malware. Earlier versions of this malware relied on tricking users into running an installer, or approving a request for permission to execute, but that has all changed now. The malware moved from being a simple trojan that relied on tricking people into running it, to a fully automated attack requiring no user interaction. The reason for this transformation is that the malware started to use flaws in Java, first, old vulnerabilities that were patched ages ago, so only affecting people who don’t keep their computers up to date, but this week, attacking flaws that Apple had, at the time, not yet patched. This means that for a few days, even the most diligent Mac users could have been hit.
This infection has no noticeable symptoms, and did not require you do do anything “stupid” to get infected. Any Mac user, not matter how careful, could have been infected. So, you need to check to be sure you are not one of the half million plus victims! Read more
Nov
25
Perl DBD::mysql on OS X Lion
Filed Under System Administration, Computers & Tech on November 25, 2011 | 12 Comments
I ran into a problem this week when the perl libraries for accessing MySQL databases refused to work on Mac OS X Lion. I did a ‘regular’ install:
- Install the 64bit version of MySQL Community Server (being sure to use the .dmg version so as to get the .pkg installer)
- use CPAN to install the needed database libraries:
$ perl -MCPAN -e shellcpan[1]> install Bundle::DBIcpan[1]> install DBD::mysql
There were no errors during the install, so I assumed all we well, until I tried to actually use the libraries to access a database that is! Using DBI to try connect to a MySQL database gave the following error:
install_driver(mysql) failed: Can't load '/Library/Perl/5.12/darwin-thread-multi-2level/auto/DBD/mysql/mysql.bundle' for module DBD::mysql: dlopen(/Library/Perl/5.12/darwin-thread-multi-2level/auto/DBD/mysql/mysql.bundle, 1): Library not loaded: libmysqlclient.18.dylib Referenced from: /Library/Perl/5.12/darwin-thread-multi-2level/auto/DBD/mysql/mysql.bundle Reason: image not found at /System/Library/Perl/5.12/darwin-thread-multi-2level/DynaLoader.pm line 204.
After a lot of googling I found plenty of people with the same problems, including people on Snow Leopard, so I figured this was not a new problem. I tried a number of the suggested solutions, and most did not work, but after two days of trying, I found one that did, and it was wonderfully simple!
The problem is that the MySQL libraries are not in the OS’s library path, so they are not being found, most of the proposed solutions tried to tackle the problem at compile time, or to use simlinks to hack the libraries into the path, but like I say, these solutions didn’t work for me. What did work is simply updating the library path in my environment!
If you run the command below before executing your Perl script the library is found and all is well!
export DYLD_LIBRARY_PATH="/usr/local/mysql/lib:$DYLD_LIBRARY_PATH"
It’s a little awkward to do this all the time, so I added the line to my ~/.bash_profile file, and now it just works for me!
I spent two frustrating days trying to fix this, so hopefully I’ll save others some time by sharing my solution.
Aug
19
OS X Lion – Maybe it’s not ‘iPadification’ but ‘Startrekification’?
Filed Under Computers & Tech on August 19, 2011 | 6 Comments
With the release of Lion there seems to be wide-spread fear, bordering on panic in some quarters, that it’s the start of the end of the Mac. The feeling seems to be that Steve is pushing us all towards iPads and iPhones, and that he’s going to leave all us power users in the lurch. Sine Apple watching is so much like Kremlinology, we can’t just ask Apple PR where they are headed, we have to infer and imply based on the past and the present. The doom-sayers are projecting a future where Apple dumb-down their desktops and laptops to the point that they have no more power than their iPhones and iPads. When I look at the same past and present, I see Apple moving towards a very different future, not one where Macs become iPad-like, but one where Apple unify the look, feel and design philosophy across all their computing products, but where no features are lost. The best analogy I can come up with is the computing experience aboard the Star Ship Enterprise (the D of course), Apple are not moving to ‘iPadify’ the Mac, they are moving to ‘Startrekify’ their entire line.
Jul
1
Getting ClamXav to use a Proxy Server
Filed Under System Administration, Security, Computers & Tech on July 1, 2011 | 4 Comments
I’ve been looking at different free Mac AV solutions so that I can make recommendations to less-computer-savy family members, and this afernoon I decided to give ClamXav a go. I’d tried it a few years ago and wasn’t very happy, but I’d been told by friends that it has improved a lot since, and a first glance at the GUI suggests they’re right. Unfortunately I didn’t get very far with my initial testing this afternoon because I’m in an environment where I have to use an HTTP proxy server to access the net, and ClamXav appears not to support proxies at first glance. It ignores OS X’s system-wide proxy settings, and it has no interface elements of its own to allow you to specify a proxy server manually. This implies that ClamXav doesn’t support proxies, but it actually does, they just didn’t bother to expose that functionality through the GUI.
ClamXav is just a GUI wrapper for the free and open source Clam AntiVirus toolkit, and it uses Clam’s regular auto-updating tool freshclam. Although the ClamXav GUI doesn’t give you control over the variables in the freshclam configuration file, that file does exist as part of ClamXav (/usr/local/clamXav/etc/freshclam.conf), and if you edit it manually it will respect the settings specified in that file. If you’re not afraid of the Terminal, you can easily edit this configuration file manually to get ClamXav to use a proxy server for updates.
Apr
21
Where Does DropBox Store the Host ID on Mac OS X?
Filed Under System Administration, Security, Computers & Tech on April 21, 2011 | 4 Comments
The technosphere is a buzz this week with the news that DropBox’s security has a rather large and rather stupid hole in it. I’m only going to give a brief overview of the issue here, so if you’d like more details please check out the blog post that broke the story. What I do want to say is that this is a really infantile mistake on DropBox’s part, and the fact that they could overlook something so elementary for so long worries me a lot.
Anyhow – the whole problem revolves around the Host ID which DropBox uses to identify a computer within your account. This code acts as both an identifier and a password, and it’s a big long string of random looking gibberish. The problem is not that this ID is easy to guess, but rather that it’s not tied to any particular machine. If a bad-guy gets their hands on the file containing this ID they can effectively clone your machine in DropBox’s eyes, and see your files in perpetuity, regardless of how many times you change your password. The only way to kill the bad guy’s access would be to de-authorise the machine who’s ID they cloned in your account pages on the DropBox website.
The original blog post that broke this story describes in detail where you can find this ID on Windows, but doesn’t mention any other OSes. Quite a few listeners to my various podcasts have asked me if I know where the file is located on the Mac. I didn’t, but I figured it would be worth spending a little time finding the answer.






