Oct
12
Protecting Yourself from Click Jacking
Filed Under Computers & Tech, Security on October 12, 2008 at 3:57 pm
‘Click Jacking’ is the latest browser-based security problem to crawl out of the wood work. Since it’s entirely browser based it affects everyone, regardless of their OS, not even Linux users are safe from this one! This is a cross-browser problem and also affects Flash. The technical details have not been released yet, but there is a proof-of-concept exploit doing the rounds. The basic idea is very simple, trick people into clicking on something you want them to click on but they don’t want to click on. From what I’ve been able to piece together from reading various blog postings and reports the attack uses CSS and iFrames to place invisible content over visible buttons or links. When the user clicks the button or link they see the click gets diverted to what ever is in the invisible layer above it instead. If you can do it by clicking the mouse, then you can be tricked into doing it with Click Jacking.
The proof of concept demonstrated how a simple web-based game could be used to turn on the user’s webcam and mic and transmit the sound and video to the attacker without the user ever seeing the flash warning asking for permission. Their clicks were hijacked to actually approve this action without their knowledge. Messing with Flash behind your back is one thing, but the technique can be used on regular web pages too. Since it’s running in your browser the attacker has access to anything you’re logged in to. They could hijack your clicks to reprogram your router, mess with your FaceBook profile, or interact with your online banking! The only slight silver lining is that attacks are limited to things that can be done by clicking.
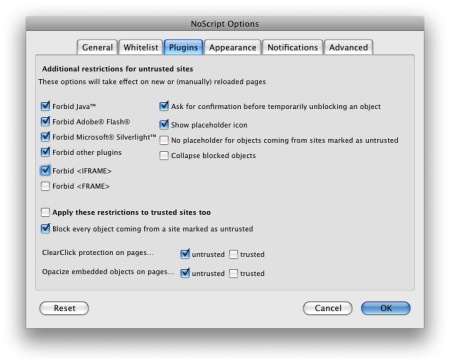
When it comes to protecting yourself the consensus seems to be that the NoScript FireFox plugin can provide near-complete protection if it’s properly configured. The default configuration will provide no protection, and you are un-protected on any sites that you allow permission to use iFrames. It’s also very important to note that this is NOT a JavaScript vulnerability. Turning off JavaScript provides no protection at all as the attack doesn’t use JavaScript, just CSS and iFrames. The reason the default NoScript configuration won’t protect you is that it allows iFrames. You need to open the NoScript Options window (you can open it by clicking on the NoScript icon in the status bar at the bottom of your FireFox window), go to the Plugins tab, and check the Forbid <IFRAME> option. You will now be protected on all sites you don’t white-list.
Finally, some researchers are advising that you have a separate browser which you will only use for your internet banking. This is a sensible precaution, and is very easy to do on the Mac, just create a Fluid App for your banking website.
There will be Flash updates and browser updates to address Click Jacking too, but they’ll take time to come out, so it seems wise to take immediate action by switching to FireFox with NoScript to protect yourself in the short-term.
If you’re interested in reading more about Click Jacking then this Securosis Article is a good place to start.







[…] impressions of iPhone now that he has one in his hot little hands. Bart Blog Post on Click Jacking: http://www.bartbusschots.ie/blog/?p=1104, and his first iPhone experiences: […]
Yikes, thanks for this post!
Is it just iFrames that are a danger or all frames?
Just iFrames I believe.
Bart.
Why not just warn users they should log off any websites they have to signed in to?
Because that wouldn’t give you full protection. NoScript lets you see the hidden elements you would be clicking on. That’s protection. Hoping you always remember to log out and hoping that nothing that doesn’t need a login can do anything you don’t want to do doesn’t strike me as appealing.
BTW, if people find the JavaScript blocking in NoScript annoying you can turn that off and still get projection from Click Jacking.
Bart.
thank you for speaking in layman’s term…
Bart – using Firefox 3 (on tiger) and last night a popup appeared saying that my system needed cleaning, couldn’t get rid of the popup – force quit was greyed out, so had to click on cancel in the popup window. Am I now at risk? do you suggest I wipe my mac mini G4 and start again? thanks..
Hi James,
I really can’t tell from that description what happened. Were you running low in disk space? If you were it could well have been a genuine OS X popup that just happened to come up while you were on the web. It may not have been related to FireFox at all.
If you’re very worried perhaps consider installing something like ClamXAV and running a scan.
Bart.
Bart – thanks a quick reponse.
It was like this one – but said something about a virus and asking me to install some anti virus/system performance software.
http://img133.imageshack.us/img133/2062/wtfam2.jpg
sorry more like this one –
http://i26.tinypic.com/1b5w6.jpg
Hi James,
They look like regular JavaScript popups contained within the browser. Chances are they were for the “benefit” of Windows users and that you’re perfectly safe. No guarantee of course, but I personally wouldn’t be too worried.
Bart.
Thanks Bart – and thanks for your invaluable contribution to the International Mac Podcast.
On a side note I get differing opinions if Leopard would be slower on my mac mini than Tiger (G4 1.25ghz, 512mb, 40gb HD). The 40gb HD could be a problem though, I bet leopard takes up more space than tiger.. got 9gb free ATM.
Hi James,
I actually do run Leopard on my G4 Mac Mini, but it has a Gig of RAM and an 80GB drive. If you only have 9GB free you’re probably better off on Tiger, and if you don’t have a Gig of RAM you’re DEFINITELY better off on Tiger.
Bart.
Duh. Seems as if they need to patch the css code in browsers to not allow z-indexing and or display:none on iframes, which sucks, but is better than say “disable all css” option in the webdeveloper toolbar for firefox. I so miss the ol’ bbs’s..
It is all click jacking and we might see more such attacks in future.
The quickest fix for this attack is – DO NOT let your site be loaded in an iframe. Thats it!
if (window.parent.frames.length>0)
{ //you are framed.
//Go to your site without frame window.parent.location=location;
}
Unfortunately that code doesn’t provide any protection to end users really. It would only protect from click-jacking if every site on the net contained it. What are the chances of that!
Bart.
[…] using the computer never knows anything has happened until it is too late. A more technical description of click jacking can be read […]
Hi, a while ago, I believe I was Click-Jacked and Like-Jacked through Facebook by clicking on a video link about April’s Fools Day. I searched online and followed all instructions to protect myself for the future by downloading NoScript, and I deleted the link from my profile. Please let me know if there are more things I can do, and what other possible threats could I face other than the ones you mentioned. Thanks
Cheers
Hi MB,
Installing NoScript will offer a lot of protection. However, FaceBook is very much the lion’s den. I’d argue that you can’t be safe and use Facebook, but I think it’s a risk the vast vast majority of people are happy to take. Best advice I can give is to be ever vigilant, be suspicious of anything that ever asks for any important information, no matter who it appears to come from, and never ever install anything sent to you over FaceBook.
Bart.
Hi Bart,
Thank you for you reply! Much appreciated. About Facebook, I have already learned my lesson, so I wont be clicking on anything suspicious there! But the question is, is there a way to protect my computer since I’ve already been click-jacked? So far nothing happened, but how would I be sure nothing will?
Cheers